Intelice Solutions: Blog
Experts Rush to Get Ahead of New Ransomware Attacks
Ransomware is now a household name, and there’s no going back. Even though cybercriminals have been using ransomware for years now, it wasn’t until the global WannaCry attack that awareness reached critical mass.
Doctors and nurses went to work as usual last May in the UK’s Central Manchester University Hospital, but when they went to turn on their computers, all computer systems began crashing. Messages began to pop up on their computer screens demanding $300 in Bitcoin in exchange for restored access – the WannaCry ransomware had struck.
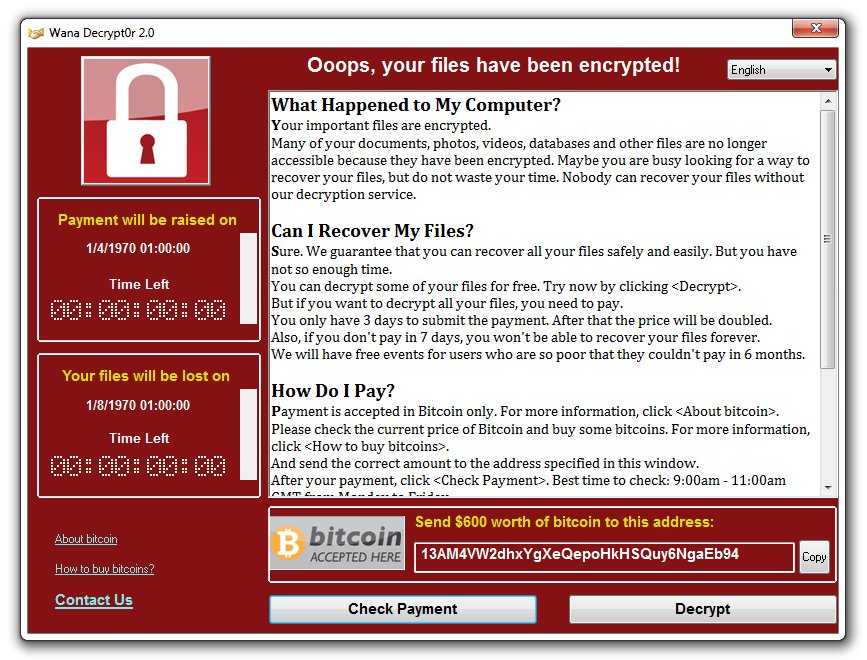
Targeted Manchester hospitals claimed that no patient info was compromised, but they did have to suspend services. The BBC reported that other hospitals in London, Nottingham, Hertfordshire, and Blackburn had also been attacked and that some phone systems went down for a period of time. Doctors and nurses were forced to use pens and paper to keep track of patient information. Once medical organizations across the UK had realized what was happening, some of them disconnected from servers at the National Health Service to try and avoid being attacked.
Exploiting Microsoft’s Operating System
This is just one of the many stories that have unfolded over the last year where large organizations were targeted with one of the largest ransomware attacks in history, named “WannaCry”. Though experts did not know this at the time, WannaCry is a ransomware cryptoworm developed by North Korea and aimed at Microsoft operating systems.
Though it seems unbelievable, there have now been more than 100 attacks like this across 150 countries just this past year. Most anti-virus software makers have scrambled to get ahead of these attacks. Once Microsoft’s experts had found that the attacks took advantage of a Windows vulnerability, they quickly released patches for computers running all versions of the operating system, including older versions such as Windows XP, Windows Server 2003 and Windows 8.
Kurt Baumgartner, at the security firm Kaspersky Lab, explained how effective and how quickly WannaCry ransomware can strike.
“Affected machines have six hours to pay up and every few hours the ransom goes up,” said Baumgartner. “Most folks that have paid up appear to have paid the initial $300 in the first few hours.”
Other experts in the field of Cyber Security found evidence that these attacks were made using a variation of the malware called, “Wanna Decryptor”. This program is a Trojan virus that utilizes AES-128 encryption to make all files inaccessible to users.
Though many of the ransomware attacks were launched against the UK, Russia, Taiwan, and Ukraine, global firms like FedEx have come under assault as well. Officials from Europol said that the attacks were of an “unprecedented level and require international investigation.”
Meanwhile, China reported a massive attack against PetroChina that took some time to resolve; as a result, customers were forced to pay cash at all PetroChina gas stations until the ransom had been paid.
Spain also reported an attack against Telefónica, a large telecom organization. Their experts were able to determine that the attacks were spread through a vulnerability called “EternalBlue.” Their IT department quickly created a patch to prevent the bug from spreading.
Controlled Folder Access For Windows 10
All of these attacks were launched against Windows-based systems, leaving IT security experts at Microsoft to take quick action to develop and release patches and other tools to stop cybercriminals. The fall updates to Windows 10 included many new improvements aimed at providing a much higher level of protection. One of these, known as Windows 10 FCU, has proven especially useful. Also known as Controlled Folder Access, this update protects files and folders from ransomware attacks using a simple methodology.
The exploit is based on the fact that most Windows programs have access to all files and folders on a computer system, which made it much too easy for hackers to gain access to those files and wreak havoc. Unrestricted access to files and folders might be convenient for users, but it opens the door to virus and ransomware attacks.
Customizing Your Operating System
Though many users are not aware, Windows gives you the ability to greatly customize your operating system, including the capability to take action to protect your data from hackers. Using Controlled Folder Access, you can modify access to your important data, so that these files are given an extra layer of protection. If any program tries to modify files that have been placed in the “protected folder”, they will be blocked. This feature is found in Windows Defender.
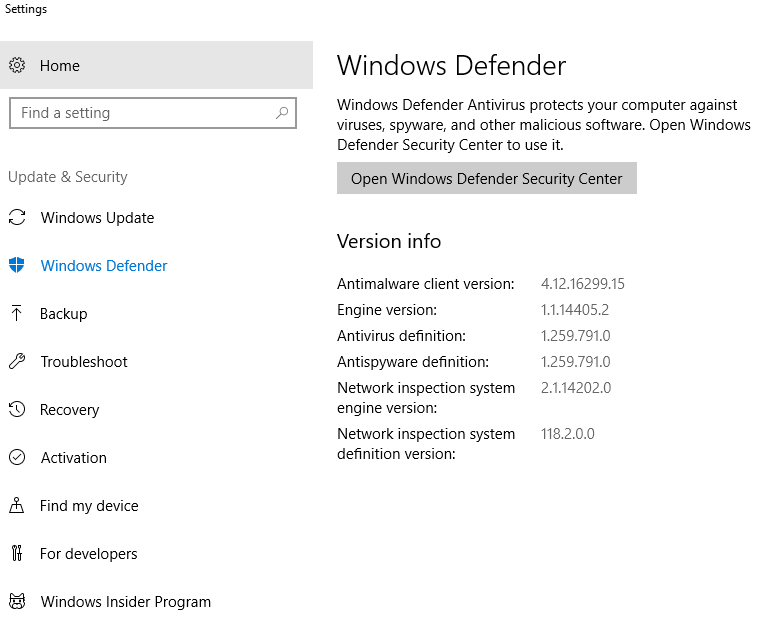
Follow these steps to enable Controlled Folder Access on your computer:
- Type Windows Defender in your start menu. This opens the Windows Defender Security System.
- Navigate to the left panel and find Virus and Threat Protection. If it isn’t listed there on the left, then type “virus and threat protection” in the settings search box at the top left.
- Click on Virus and Threat Protection Settings. This may appear in a new dialog box or on the right side of the Virus and Threat Protection page.
- Scroll down and find “Controlled Folder Access”. Toggle the button to “On”. This enables the Controlled Folder Access feature.
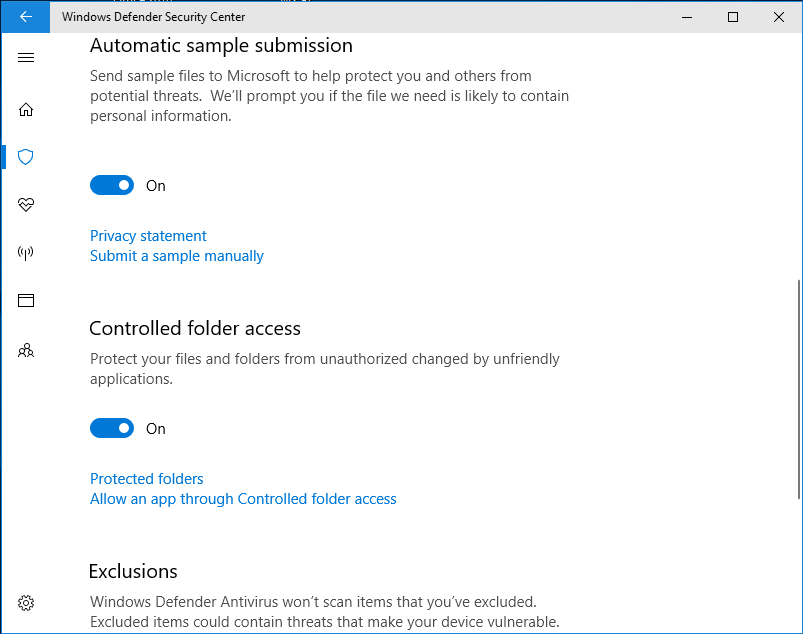
Granting manual access to programs
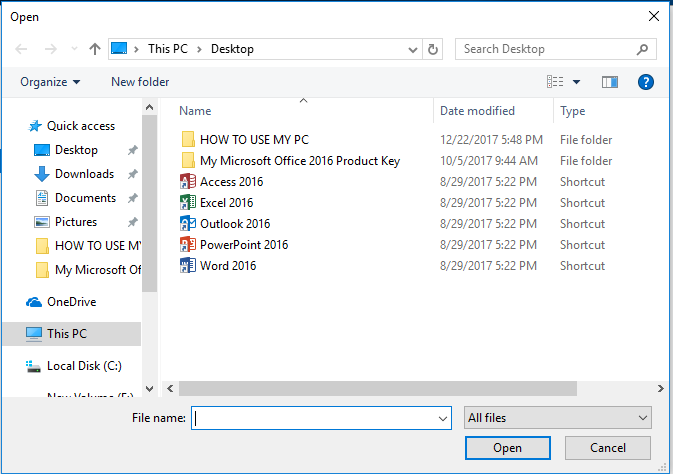
The most significant drawback to using this feature is that some of your favorite apps or programs may be blocked. The solution is simple: Manually grant access for these programs. Just below the toggle button, you’ll find a link called, “Allow an app through Controlled folder access”. Click on that and a new dialog box appears. Now click the “Plus” sign out beside “Add an allowed app”.
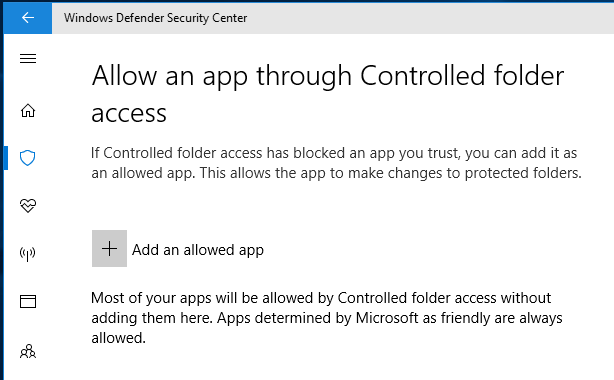
The familiar “Open a File” window on your computer will automatically open, giving you the ability to click on whatever file, folder or program you would like to exclude. Navigate to the EXE file and then click on “Open”. You have successfully added this program to your exclusions list.
This works for all your favorite programs like Photoshop, Dragon Naturally Speaking, and Quickbooks. Please note that Windows has its own list of “safe” programs that are already included, so there’s no need to grant manual access to programs like Excel and Publisher.
For more information about the latest IT security threats and how to protect you and your business against them, get in touch with our team of cyber security experts.




