Intelice Solutions: Blog
Common Causes for Cybersecurity Claim Rejections: Understanding the Reasons
Cybersecurity insurance is an essential component of any organization’s risk management strategy. It is designed to protect businesses from financial losses that arise from data breaches, cyber-attacks, and other security incidents. The insurance policy covers the costs associated with investigating,…
Read MoreCommon Causes for Cybersecurity Insurance Application Rejections: An Overview
Cybersecurity insurance is a type of insurance that protects businesses and individuals from internet-based risks. It provides financial protection against data breaches, cyberattacks, and other online threats. However, not all applications for cybersecurity insurance are approved. There are several common…
Read MoreWhat is Cyber Insurance? A Clear Explanation
Cyber insurance is a type of insurance policy that provides coverage for businesses and individuals against losses resulting from cyber attacks. With the increasing frequency and severity of cyber attacks, cyber insurance has become an essential component of any comprehensive…
Read MoreNew Year, New Cybersecurity Resolutions
2024 is shaping up to be a pivotal year in cybersecurity—have you given it any thought yet? With the integration of artificial intelligence into the technology landscape, both the complexity of cyber threats and the sophistication of security solutions are…
Read MoreYou got Phished – What Now?
Do you have a plan in place for how to respond when you suspect that you or your business has been made the victim of a phishing scam? Follow the steps laid out in this article to limit the damage and make sure it never happens again.
Read MoreDo You Know the Risks of IoT?
The ever-expanding network of Internet of Things devices offers a range of convenient benefits to consumers—but don’t make the mistake of overlooking IoT vulnerabilities.
Read MoreWhich Is the Most Secure Phone OS?
Most people think of their smartphone as a personal device that should remain private. However, as our lives move more and more online, it’s essential to have a secure phone OS that can keep your data safe.
Read MoreWhich Is the Most Secure Phone OS?
Most people think of their smartphone as a personal device that should remain private. However, as our lives move more and more online, it’s essential to have a secure phone OS that can keep your data safe.
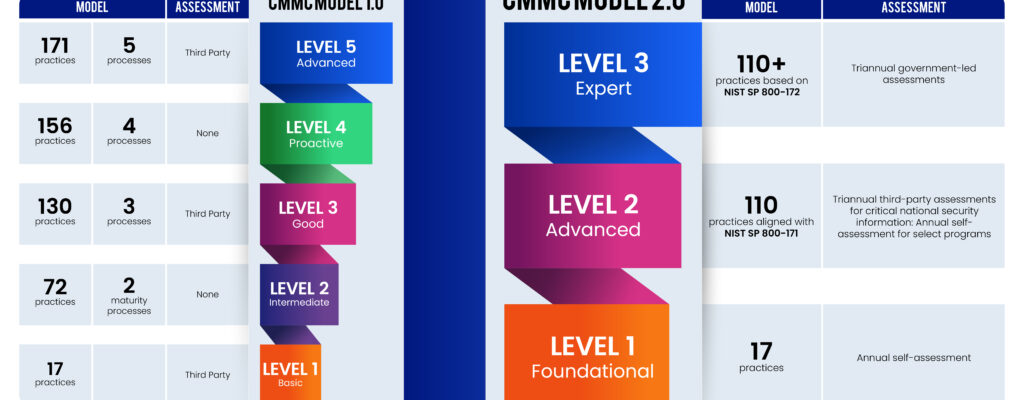
Read MoreDoD Contractors—Do You Know What These CMMC Updates Mean For You?
The DoD just released CMMC 2.0, which drastically changes compliance expectations for contractors over the course of the next year.
Read MoreSmall Businesses Under Direct Attack From SEO Poisoning
Cybercriminals understand SEO and are now using it to hack unsuspecting users. There are two common ways SEO poising occurs.
Read MoreRecent Posts
How can we help?
Whether you need immediate help with an IT issue or want to discuss your long-term IT strategy, our team is here to help.
Call us at (301) 579-8066 or complete the form below and we'll help in any way we can.
"*" indicates required fields
Categories
- 2020's Rewrites
- Advanced Cybersecurity
- Blog
- Company News
- Compliance Articles
- COVID19
- Cybersecurity Alerts
- Cybersecurity Awareness Month – 2022
- Cybersecurity Insights
- Cybersecurity News
- Financial Management Systems
- Financial Management Systems
- Financial Management Systems ERP Solutions Articles
- General Business Insights
- Industry News
- Industry Reports
- Intelice Case Studies
- Intelice News & PR
- Intelice News & PR
- Intelice's Solution
- IT Services In Washington DC Metro
- Managed IT Services Articles
- Managed Security
- Meet The Team
- Microsoft 365
- Microsoft Business Central
- Microsoft Office
- Microsoft Teams
- Microsoft Tips & Tricks
- News
- Newsletter
- Optimize Blog
- Our Partners
- Tech Tips
- Technology Education & Information
- Testimonials
- Video Library
- Webinar Replay